
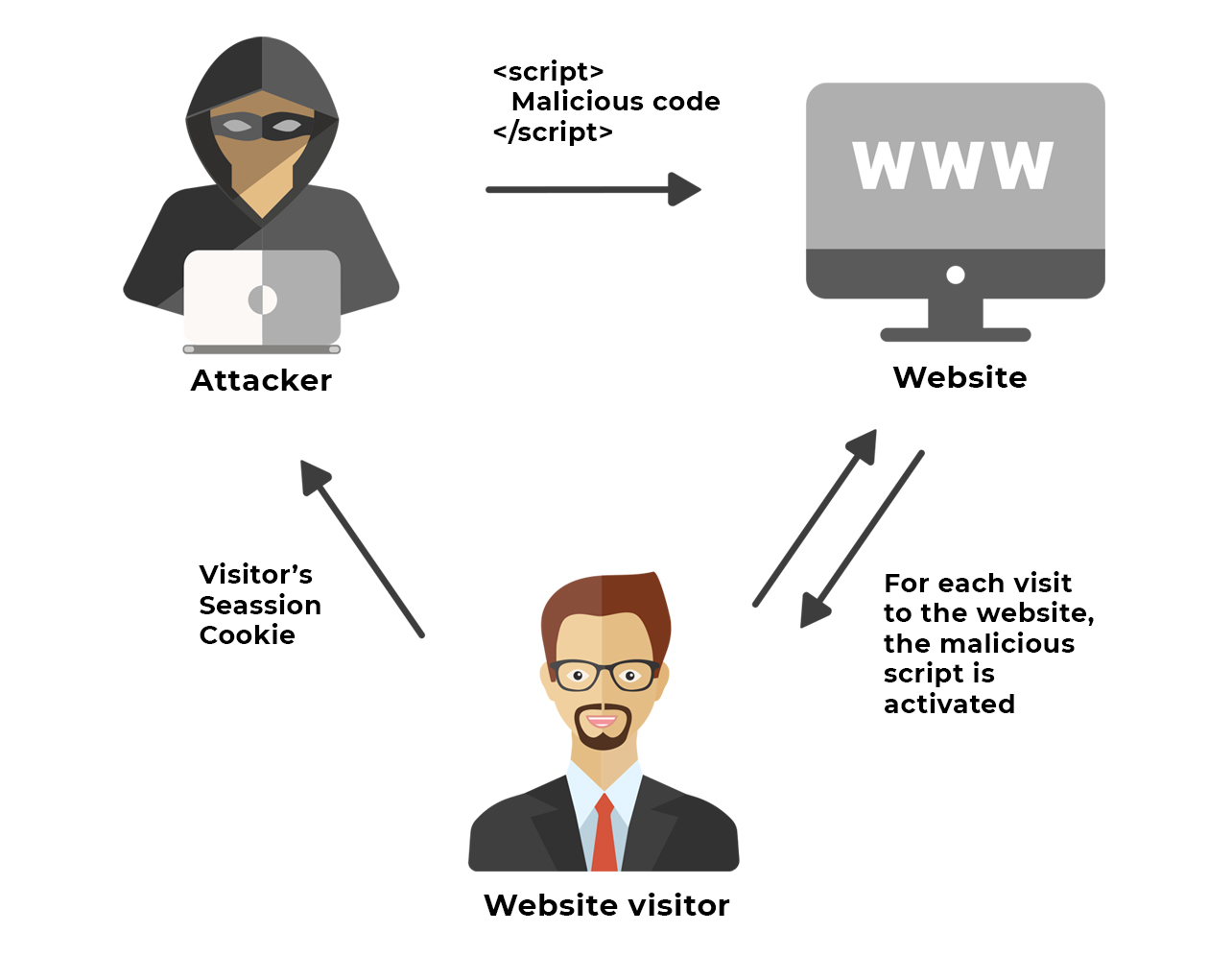
Cross-site Scripting (also known as XSS) is a web security vulnerability that allows an attacker to compromise the interactions that users have with a vulnerable application. XSS is a client-side code injection attack. The attacker aims to execute malicious scripts in a web browser of the victim by including malicious code in a legitimate web page or web application.
Cross Site Scripting vulnerabilities are the most common vulnerability found in WordPress plugins by a significant margin.
The actual attack occurs when the victim visits the web page or web application that executes the malicious code. Commonly used for Cross-site Scripting attacks are search inputs, forums, message boards, and web pages that allow comments. Basicly any unsanitized user input. Most common attacks are done by adding malicious JavaScript code in inputs thet gets executed inside a victim’s browser.
Preventing cross-site scripting is trivial in some cases but can be much harder depending on the complexity of the application and the ways it handles user-controllable data.
The following suggestions can help protect your users against XSS attacks:
Sanitize user input:
Validate to catch potentially malicious user-provided input.
Encode output to prevent potentially malicious user-provided data from triggering automatic load-and-execute behavior by a browser.
Limit use of user-provided data:
Only use where it’s necessary.
Utilize the Content Security Policy:
Provides additional levels of protection and mitigation against XSS attempts.
Regularly use a web vulnerability scanning tool to identify XSS vulnerabilities in your software.
While thease type of attacks continue to grow and have success, especialy on WordPress web sites, a bit od testing and usage of methods such as the above listed, is a great way to protect users of your application from the majority of XSS attacks.